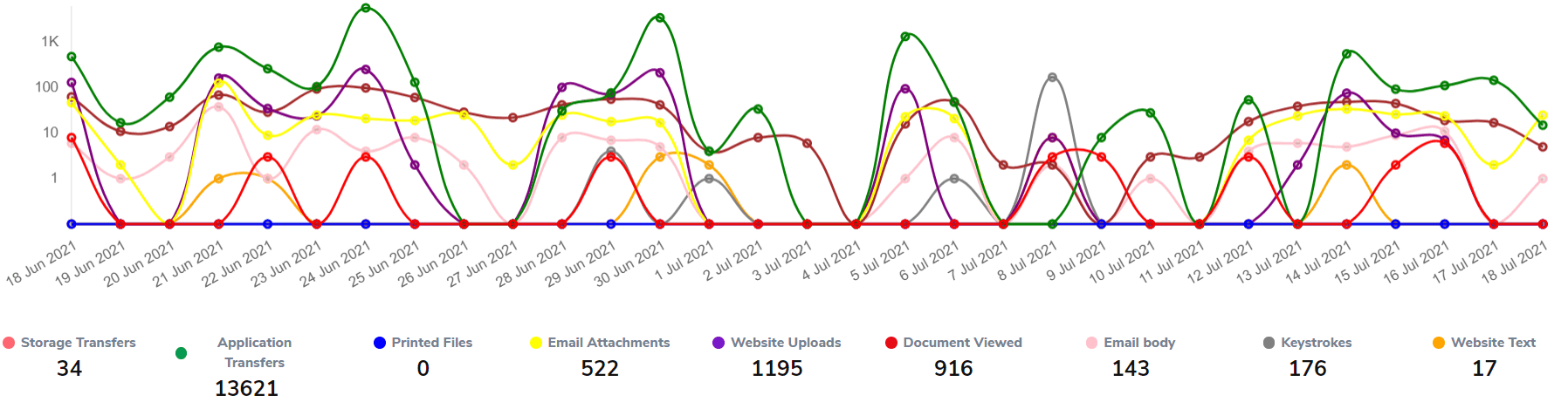
Covers wide range of user behaviours
User and data risk assessment tool for Cyber-Security Professionals
User assessor monitors how users access, store and move data and highlights risky behaviours.
Detects risky handling of PII and Credit card data inline with regulations and standards like NDB, GDPR and PCI DSS. Helps to assess organisation's conformance to ISO 27001 and ACSC's Information Security Manual (ISM).
User Assessor uses specialised techniques to target company's Intellectual Property and highlight risky user actions.

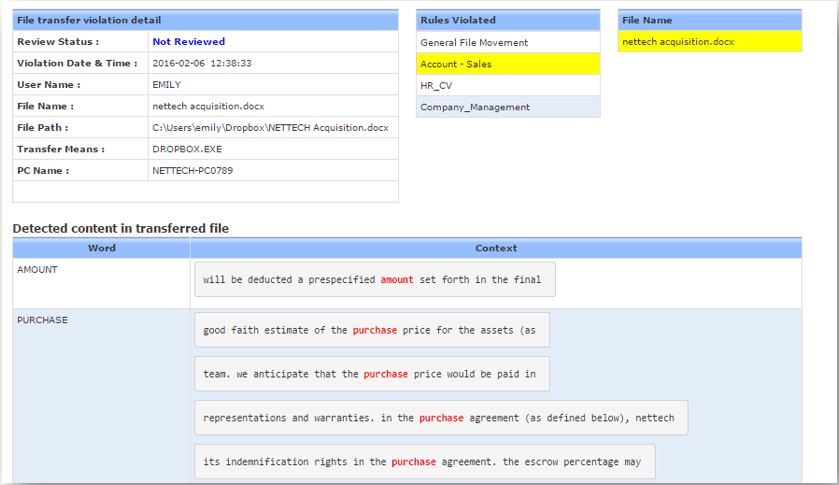
Content level monitoring helps to focus detection of sensitive PII and company IP. For example knowing the data sent out had credit card information can help to highlight serious non-compliances. Without it IT teams struggle to establish the level of risk from just flow of data. User assessor offers several ways to tag information for detection. These include:
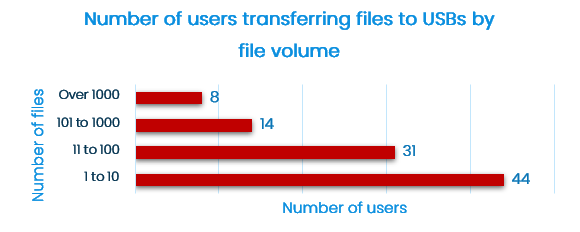
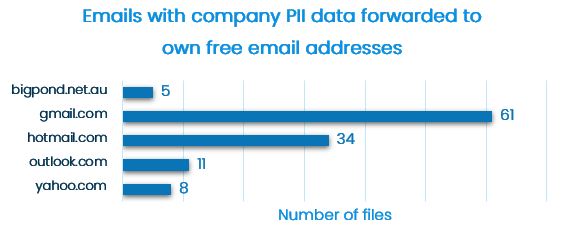
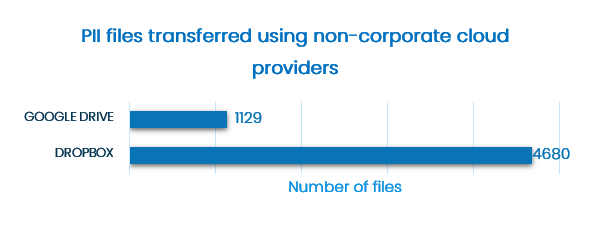
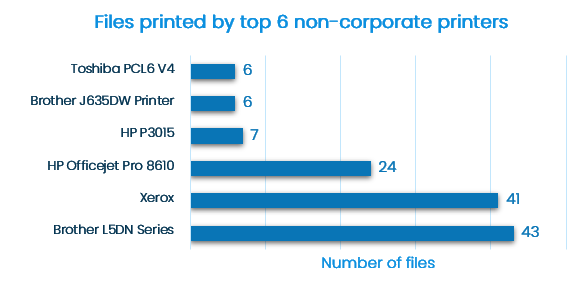
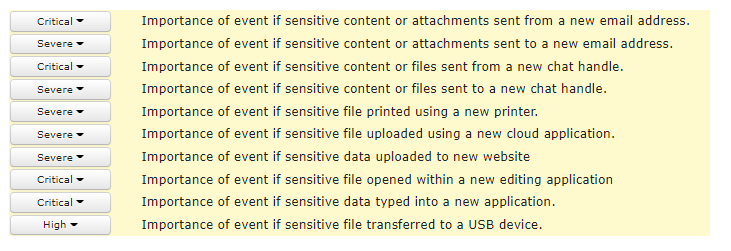
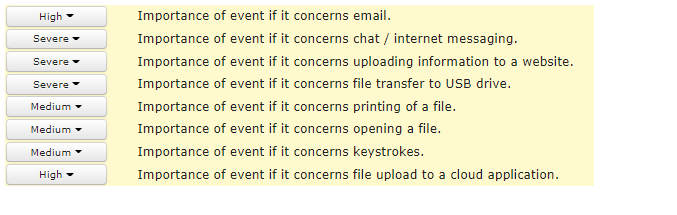
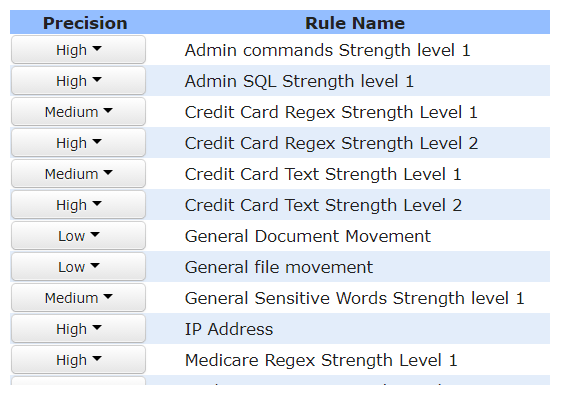
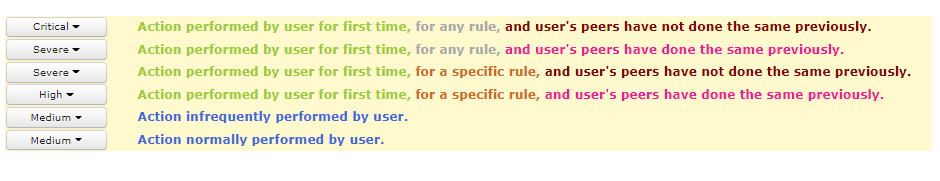
Default settings consist of predefined templates for monitoring data related to privacy regulations and security standards. The default settings can be easily extended to capture company’s IP and specific data sets.
A lightweight scanning agent is deployed to representative end-points and servers. The same agent is used to perform remote data discovery function.
The agent monitors users' behaviour and how sensitive unstructured data is being used, moved, and stored by users on all corporate and non-corporate channels, including online and offline media.
Generates detailed reports highlighting potential sources of user risk. Reports are highly customisable to focus on specific issues as required by the customer.

Mobirise page builder - Check it